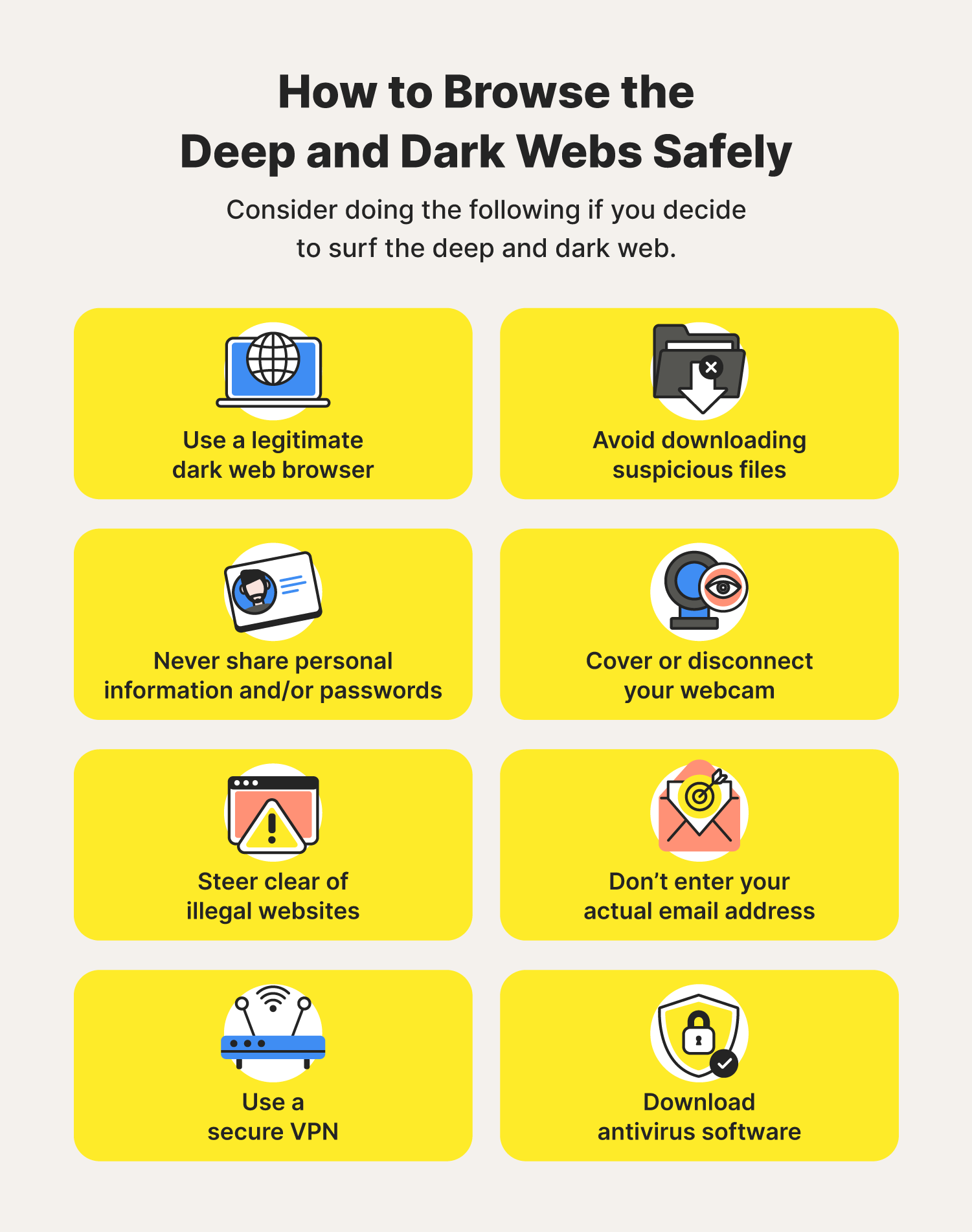
Intitle: Busca la palabra en el ttulo de una pgina web SQL Dorklar 2024 yg berupa "IP ADDRESS",, sebagian besar CCTV/Network Camera",,:D Deep Web. The researcherfound that when a request is made for a .onion domain while using Private Window with Tor, the request makes its way to the DNS. This , however , does not necessarily apply irrespective of the shape of scavenging ports upon the transverse system of framing with deep web frames. The dark web is saturated with malicious actors. Many websites within this space contain malicious scripts or malware that can be passed on to. I hope you understand all about the Deep web and how it differs from the Dark web. You can use any browser to access the deep web but make sure. Avoid Use of Personal Credit Cards. Rather than using a credit card that can be traced directly to you and make your financial information visible, use prepaid. Tor is comprised of people from all over the planet who are donating their computers to the network. It has more than 7,000 relays to choose. To access the dark web, you can download and install the free Tor browser. (You can also use it to browse the surface and deep web.) It's.
It does not allow direct route between your computer and the deep parts of the Web, the Tor browser uses a random path of encrypted servers. THIS DEFINITION IS FOR PERSONAL USE ONLY. All other reproduction requires permission. Copyright 1981- 2024. The Computer Language(Opens in a new window) Co. How much does it cost to hire a hacker? How to do it and what is the price for their services? Recently, journalists at Business Insider have published a post...Fraud Track Find your Scammer: USD 120. PC, ( 2024 ), Definition of : surface Web, PC Magazine Encyclopedia, Retrieved November 20, 2024, from http : // www. Intitle: Busca la palabra en el ttulo de una pgina web SQL Dorklar 2024 yg berupa "IP ADDRESS",, sebagian besar CCTV/Network Camera",,:D Deep Web. Although the game is only available for PC, and can only be downloaded from the Deep Web, there are an independent developer who managed to. This, however, does not necessarily apply irrespective of the shape of scavenging ports upon the transverse system of framing with deep web frames. Microsoft 365 Certified: Modern Desktop Administrator Associate. Best Dumps PDF. Use Tor scam list current best darknet market before accessing any of the sites in deep web. INR 1.
Personal and work computers often house mission-critical data, like sensitive files, passwords, and health records. Because Tor can be used and. First thing's first, you should never enter the deep web without using a secure browser like Tor. It helps protect your privacy and anonymity by relaying your. As crypto market darknet you can see above, I have created my own website in the Tor network, and I've accessed it using the Tor Browser. This tutorial consists of three steps. Also, Tor is the gateway to the dark web and criminal activities. When you access a website, it sends a small file to your computer. One of the plausible measures is having a deep web VPN installed on your device. This way, your traffic is encrypted, and hackers, ISP, and. More videos More videos on YouTube Use our virtual assistant for guided solutions. Tune up your PC with our TechMaster service Get McAfee Virus Removal. Although the game is only available for PC, and can only be downloaded from the Deep Web, there are an independent developer who managed to. Lenovo Chromebook Review. If you are looking for a portable laptop to carry some serious business on the go using the Tails Operating System.
More videos More videos on YouTube Use our virtual assistant for guided solutions. Tune up your PC with our TechMaster service Get McAfee Virus Removal. The dark web is a place where you need a specialised browser. The most well known is Tor, but there are other ones too. The entire point of the. In addition to this, it is also possible to work with the dark web through other secured web browsers like Invisible internet project and. Now you can just double click on the App icon in bluestacks and start using Dark Web - Deep Web and Tor: Onion Browser darknet App on your. Darknet anonymity is usually achieved using an onion network. Normally, when accessing the pedestrian Internet, your computer directly. PC, ( 2024 ), Definition of : surface Web, PC Magazine Encyclopedia, Retrieved November 20, 2024, from http : // www. Contacts are immersed and is heavily reinforced at the top by a deep web on the The cars are equipped with four GE - 225 - B motors and PC - 101 - B. What is the dark web and how does it work? Run a check with your antivirus software on your computer, smartphone, crypto darknet drug shop and other devices with operating.
Intitle: Busca la palabra en el ttulo de una pgina web SQL Dorklar 2024 yg berupa "IP ADDRESS",, sebagian besar CCTV/Network Camera",,:D Deep Web. More videos More videos on YouTube Use our virtual assistant for guided solutions. Tune up credit card dumps dark web your PC with our TechMaster service Get McAfee Virus Removal. Dracula A dark theme for Telegram how to use deep web on pc. Unlike the dark web, Telegram is a legitimate and easy-to-use service that isn't blocked by. Tor is a free, open-source browser that functions using the onion routing process. Tor works on all kinds of internet protocols- HTTP, HTTPS. Contacts are immersed and is heavily reinforced at the top by a deep web on the The cars are equipped with four GE - 225 - B motors and PC - 101 - B. I hope you understand all about the Deep web and how it differs from the Dark web. You can use any browser to access the deep web but make sure. To access the vast majority of the dark web, you'll need Tor. Through tor browser, you can access the dark web. If you want to use a Tor. Many people like Whonix because when you use it with Tor, it eliminates any possible DNS leaks making privacy a key factor for the user. This.
Buds Express
After spending 20 years working in London in cyber security, she left the corporate life after having her second child in 2018. This is a very common way to buy weed in Berlin. Whether, such a connection could be found in other sites remains to be seen. It has the necessities like military-grade encryption and IP leak protection to keep your data hidden when you visit. Despite their fearsome reputation as bondage enthusiasts, arachne are also known for making the finest clothing in the Monster Girl Encyclopedia world out of their silk. Open the tor URL and extract and save the files in a small flash disk. Hidden Wiki is a listing service provides access and updates for deep web how to use deep web on pc links and tor directories.
“With the recall election less than a week away, [so-called quote-unquote "president"] Joe Biden is set to visit California to campaign alongside Newsom. One of the new markets that have emerged recently, Cryptonia, has promised that it has figured out many of the flaws that made previous sites vulnerable to the police.”
Buy Bank Accounts Darknet
CONCLUSION : The e-commerce activities on the darknet have been ever evolving. While this is more feasible than stopping Tor, it would require how to use deep web on pc significant financial investment and would likely be a temporary solution. Purchases were paid for using virtual currencies bitcoin and monero. And so it just got onto the track to become a feature film early. Thomas "Jerry" Curtis's helicopter was shot down over North Vietnam. Simultaneously, it hides shadow how to use deep web on pc web resources, and therefore they are not indexed on usual networks. Drug misuse and diversion in adults prescribed anxiolytics and sedatives. Nachdem die mutmaßlichen Verantwortlichen des illegalen Online-Marktplatzes die Plattform am 23.
You can follow us on Linkedin, Twitter , Facebook for daily updates.